Multi-Tenant SaaS Architecture: Complete Security Guide
Scaling from a single-tenant MVP to an enterprise-ready platform is not just about adding more hardware. It’s about preventing tenant A’s invoices from leaking into tenant B’s dashboard, proving you can enforce least privilege, and migrating to pooled infrastructure without taking the product offline. This multi tenant saas architecture guide focuses on the database and isolation layer-the schemas, RLS policies, and migration strategies we deploy on engagements like the Rails modernization case study.
Need to retrofit multi-tenancy fast? Book a technical call and we’ll map RLS, migrations, and compliance guardrails to your roadmap.
Spoke: This article focuses on the data/DB layer of multi-tenant security. For the full AI platform security architecture (APIs, RAG, agents, observability), see the pillar AI Platform Security Guide. For the retrieval layer, see RAG architecture and semantic search.
1. What Is Multi-Tenant Architecture (and Why It Matters)?
Multi-tenancy lets multiple customers share the same infrastructure while guaranteeing isolation. At one extreme you can give each tenant its own database (great isolation, terrible economics). At the other extreme, every tenant shares one database with a tenant_id column and row-level security ensuring they never see each other’s data.
Comparing tenancy models:
| Model | Pros | Cons | When to use |
|---|---|---|---|
| Single-tenant (one DB per customer) | Strong isolation, simple migrations per customer | Expensive, slow onboarding, Ops overhead | Regulated industries needing physical isolation |
| Pooled multi-tenant DB with RLS | Efficient, fast onboarding, easier analytics | Requires careful design, noisy neighbors possible | Startups & SaaS platforms needing scale |
| Hybrid (pooled + dedicated heavy tenants) | Mix of efficiency and isolation | Requires tenancy orchestration | When some customers pay for private instances |
Most SaaS companies start pooled and graduate to hybrid once a few “mega tenants” emerge. Regardless, RLS and a solid authorization layer are non-negotiable.
Core invariants for pooled multi-tenancy:
- Every row contains a
tenant_id. - Every query filters by
tenant_idvia RLS. - Every authentication token includes a tenant context.
- Every batch job sets the tenant context before running.
Get these right early, and you avoid rewriting months of business logic when the first enterprise security review lands.
Multi-Tenant Isolation Architecture
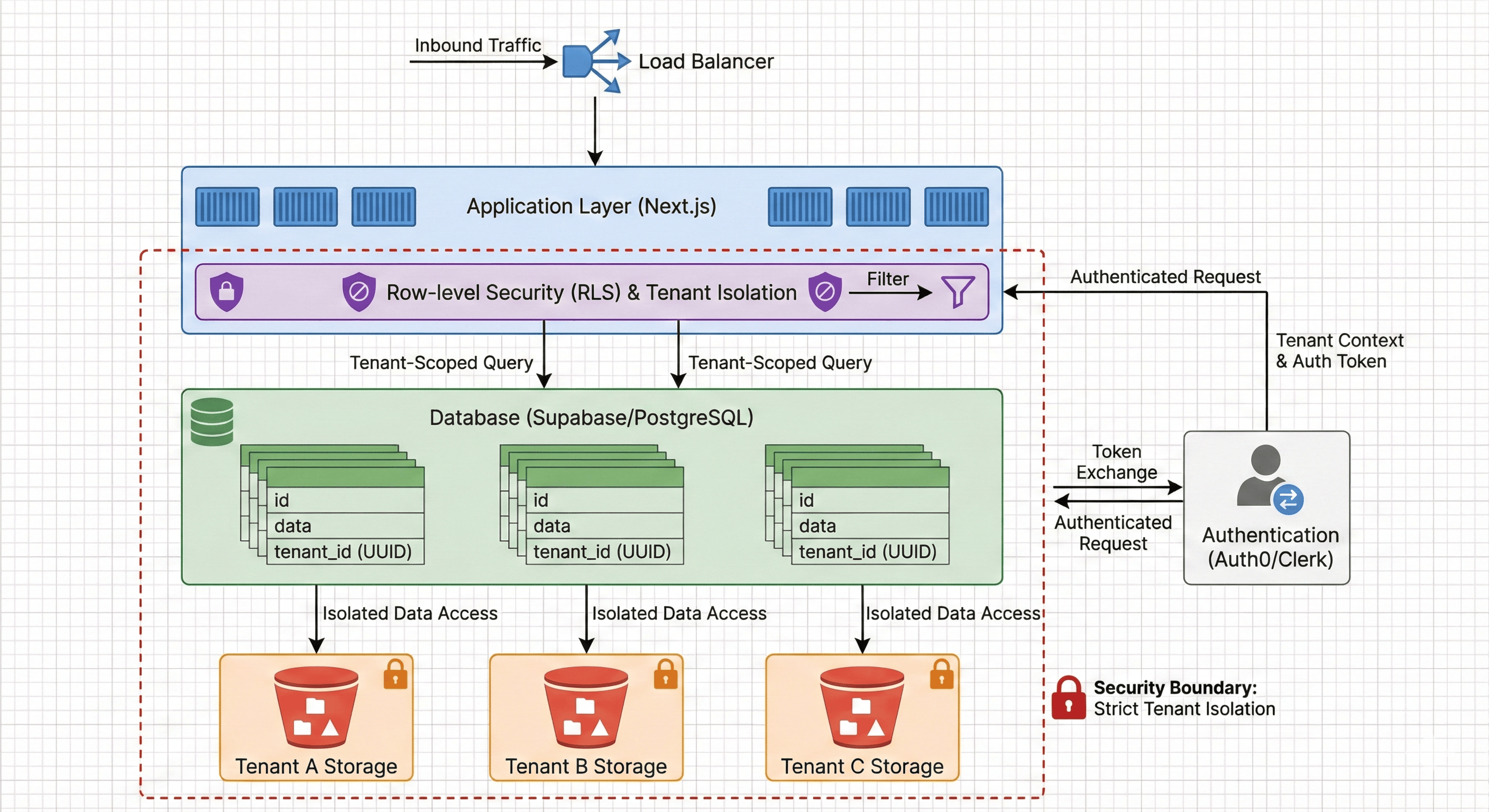
Multi-tenant SaaS architecture showing authentication, session with tenant_id, and row-level security enforcing tenant isolation.
Isolation layers:
- Authentication (teal): Validates user identity and extracts tenant context
- Database RLS (red): Enforces tenant filtering at row level - last line of defense
- Data (green): Physically separated by tenant_id, never cross-contaminated
2. Database-Level Tenant Isolation with Row-Level Security
Row-Level Security (RLS) is a Postgres feature that enforces permissions directly in the database. Instead of trusting application code to always filter by tenant_id, you let Postgres enforce that condition automatically.
Enabling RLS
ALTER TABLE document_chunks ENABLE ROW LEVEL SECURITY;
CREATE POLICY tenant_isolation ON document_chunks
USING (tenant_id = current_setting('app.current_tenant')::uuid);
-- Set tenant context per request in your middleware:
SELECT set_config('app.current_tenant', :tenant_id, true);
With that policy, every SELECT, UPDATE, or DELETE automatically filters by the current tenant. No more “forgot to add WHERE tenant_id = ...” incidents.
Where RLS Goes Wrong
- Connection pooling - ensure each connection sets
app.current_tenantbefore executing queries; frameworks like Rails or Prisma can hook into connection checkout. - Cross-tenant admin queries - admin dashboards need bypass policies. Implement a role
app.super_adminwith a separate policy. - Background jobs - queue workers must set tenant context before running tasks; encode
tenant_idin job payloads.
Real-World Win
In our Rails modernization, the platform stored thousands of documents per tenant. We enabled RLS on every table, added SET app.current_tenant in middleware, and dropped cross-tenant leakage to zero-all verified during enterprise security testing. The result: zero vulnerabilities, 800+ automated tests, and the confidence to layer in RAG features later.
3. Application-Level Authorization
RLS enforces “who can query what” inside Postgres, but you still need an application layer to:
- Parse JWTs / session tokens.
- Map users to tenants and roles (admin, member, read-only).
- Gate features (billing dashboards, AI assistants) by plan.
- Rate-limit at tenant + user level.
- Emit audit logs for every sensitive action.
Middleware flow:
1. Request hits API with Authorization header.
2. Middleware verifies JWT (Clerk/Auth0/custom).
3. Determine tenant_id + role from claims.
4. Set tenant context (e.g., `set_config('app.current_tenant', tenant_id, true)`).
5. Check permissions (e.g., can this role access `collection_id`?).
6. Continue to handler with tenant-scoped context.
For B2B SaaS we often integrate Clerk or Auth0 with organization support so users can belong to multiple tenants. Clerk’s organization API pairs nicely with row-level security: each request includes the active organization ID, which we feed into current_setting.
Authorization Patterns
- RBAC (Role-Based Access Control) - define roles per tenant; store in
rolestable withtenant_id. - Feature Flags by Plan - use PostHog or LaunchDarkly to toggle features per tenant (e.g., AI assistant only for Enterprise plan).
- Audit Logging - capture
user_id,tenant_id,action,resource,timestampfor compliance. Tools like PostHog make this easy while also providing product analytics per tenant.
4. Data Migration Strategies (Single-Tenant Multi-Tenant)
Rewriting the app from scratch is rarely possible. Instead, we incrementally migrate.
- Add
tenant_idcolumns everywhere. Backfill with default tenant initially. - Update foreign keys to include
tenant_id. Example:
ALTER TABLE invoices
ADD COLUMN tenant_id uuid REFERENCES tenants(id);
UPDATE invoices SET tenant_id = customers.tenant_id
FROM customers
WHERE invoices.customer_id = customers.id;
- Deploy RLS policies in “log-only” mode (deny writes but log violations) to catch missing tenant filters.
- Gradually onboard tenants to the new pooled DB while running shadow traffic tests.
- Cut over once metrics show zero unauthorized access.
For large documents or RAG embeddings, we sometimes use Neon branching during migration: fork the database, test RLS and multi-tenant schema on the branch, then promote once confident.
Hybrid Tenancy
When a huge customer demands isolation, we give them their own Postgres instance but keep everyone else in the pooled cluster. A simple tenancy service routes requests based on tenant_id (pooled vs dedicated). That way you keep efficiency without losing big deals.
5. Performance & Scalability Planning
Multi-tenant systems introduce “noisy neighbor” issues, so we plan for:
Partitioning & Indexing
- Partition large tables by
tenant_idor time windows (monthly) to keep indexes small. - Composite indexes
(tenant_id, resource_id)on every table used in dashboards. - Use
pg_stat_statementsto find queries missing tenant filters.
Caching Strategies
- Cache per-tenant data (e.g.,
Redis key = tenant_id:user_id:resource) to avoid cross-tenant cache poisoning. - Shared caches must include
tenant_id; never store “global” results unless they’re truly global (feature flags, configuration).
Observability
- Track P95 latency per tenant so you can spot noisy neighbors.
- Use PostHog to monitor feature usage per tenant: which features drive adoption, where do users drop?
- Build dashboards for query counts, storage per tenant, cost per tenant-critical for upsell conversations.
6. Security Testing & Compliance
Enterprise prospects will hand you 200-question security questionnaires. Be ready with:
Automated Tests
describe 'tenant isolation' do
let(:tenant_a) { create(:tenant) }
let(:tenant_b) { create(:tenant) }
it 'prevents cross-tenant access' do
create(:invoice, tenant: tenant_a, amount_cents: 1000)
expect {
acting_as(tenant_b_user) { Invoice.first }
}.to raise_error(ActiveRecord::StatementInvalid) # RLS denied
end
end
Manual Pen Tests
- Attempt cross-tenant API calls.
- Test privilege escalation (member admin).
- Run SQL injection attempts to ensure RLS still holds.
Audit Readiness
- Log every access to sensitive tables (PII, payments).
- Document RLS policies and access review processes.
- Maintain data retention/deletion playbooks per tenant (GDPR, contractual requirements).
Our security-hardened architecture pattern bundles automated scanning (OWASP ZAP, Nuclei), manual pen tests, and incident response runbooks. See the pattern
7. AI-specific multi-tenancy
Modern SaaS increasingly includes AI search, embeddings, and agents. Multi-tenancy has to extend beyond the primary database.
Vector databases & embeddings
- Namespace per tenant: Pinecone/Qdrant/Weaviate support collections or metadata filters; enforce tenant filters before similarity search.
- pgvector strategy: keep
tenant_idas part of composite primary key, add partial indexes (WHERE tenant_id = ...) for large tenants. - Embeddings pipeline: store embedding job metadata with tenant context; retry jobs independently so one tenant’s failures don’t block others.
LLM API key management
- Use a service account to call OpenAI/Anthropic but log usage per tenant. If tenants demand isolation, issue subkeys (Azure OpenAI supports this) or proxy through your own billing layer.
- Implement per-tenant spend caps with alerts at 70%/90% thresholds. When a tenant breaches, degrade gracefully (e.g., limit to cached answers) instead of hard errors.
RAG & agent isolation
- RAG retrieval should pull from tenant-specific indexes plus metadata filters (product line, region). Double-check chunk metadata before injecting into prompts.
- Agent tool registries must scope available tools by tenant and role. Log every invocation with
{ tenant_id, user_id, tool, args_hash }for audits. - MCP servers should sign manifests per tenant so malicious actors can’t enumerate admin tools.
Link these controls back to the broader security guides: see Hybrid Search Architecture for retrieval guardrails and AI Platform Security for tool/agent hardening.
8. Tenant lifecycle management
Design multi-tenant architecture as a lifecycle:
- Onboarding
- Automated provisioning: new tenant row, default roles, feature flags.
- Configure identity provider mappings (SCIM, SAML) when needed.
- Seed sample data or import from legacy systems via background jobs.
- Day-to-day operations
- Self-service admin (invites, role assignment, plan upgrades).
- Quotas per plan (storage, AI tokens, API calls) enforced and surfaced in dashboards.
- Observability per tenant (usage, errors, latency).
- Offboarding / deletion
- Soft-delete window with retention policy.
- Hard delete with point-in-time recovery window, plus log evidence for compliance.
- Export tenant data (JSON/CSV) to satisfy data portability requirements.
Automate as much of this lifecycle as possible; manual scripts won’t scale past a handful of tenants.
9. Economics & cost modeling
Understanding per-tenant cost informs pricing and when to shift tenants to dedicated infrastructure.
- Cost tracking: log compute minutes, storage usage, API calls, and AI token spend per tenant. Tools like PostHog + custom PostgreSQL tables work well.
- Pricing tiers: align features (AI assistants, analytics) with plans. High-cost features should require enterprise plans or usage-based billing.
- Dedicated instances: when a tenant consistently consumes >20-30% of pooled resources or demands custom compliance, migrate them to a dedicated Postgres instance (hybrid model).
- Noisy neighbors: use rate limiting + throttling to prevent one tenant from saturating shared queues or CPU. Alert on anomalies (3× baseline) and consider burst credits for premium plans.
10. Observability & noisy neighbor detection
Metrics to capture
- P95 latency per tenant and per route.
- Query volume, error rate, and cache hit rate per tenant.
- Resource usage (CPU, memory, bandwidth) attributed via request headers or middleware.
- AI spend (tokens, rerank calls) and corresponding revenue.
Dashboards & alerts
- PostHog/Metabase dashboards for feature usage, conversion, retention by tenant.
- Datadog/New Relic for infra metrics tagged with
tenant_id. - Alerts when latency doubles for a single tenant, or when token spend spikes unexpectedly.
Anomaly response
- Throttle specific tenants via feature flags.
- Migrate heavy tenants to dedicated resources.
- Add per-tenant circuit breakers for flaky integrations (webhooks, third-party APIs).
11. Disaster recovery & resilience
- Backups: schedule automated backups with PITR (point-in-time recovery). For pooled databases, ensure you can restore subsets (per tenant) without wiping everyone.
- Testing restores: quarterly, select a tenant and restore their data into staging to ensure backups actually work.
- Geo-redundancy: replicate read replicas across regions when compliance requires data locality.
- Runbooks: document who triggers failover, how to validate RLS after restore, and how to notify tenants.
12. FAQ
Q: When should I move a tenant to a dedicated database?
A: When they pay for isolation, have regulatory requirements, or consume so many resources that pooled performance suffers.
Q: Do I need a separate vector database per tenant?
A: Not usually. Use metadata filters/namespaces, but enforce tenant filters before similarity search and validate chunks after retrieval.
Q: How do I test tenant isolation automatically?
A: Build integration tests that act as Tenant A/B simultaneously; ensure cross-tenant calls fail. Add mutual exclusion checks using RLS + job payload assertions.
Q: How do I handle analytics across tenants if data is siloed?
A: Use a data warehouse (BigQuery/Snowflake) fed via CDC that includes tenant IDs, then apply masking and per-tenant views when exposing analytics back to customers.
Q: What’s the cheapest way to get started?
A: Pooled Postgres with RLS, Supabase Auth/Clerk for identity, and per-tenant caching. Add hybrid/dedicated setups later when needed.
13. Real-World Implementation (Rails Case Study)
In our Rails modernization:
- Assessment: Legacy single-tenant schema with customer-specific databases.
- Plan: Migrate to a pooled Postgres cluster with
tenant_idcolumns, RLS, and pgvector for new AI features. - Execution: 10-week roadmap sprint including semantic migrations, RLS rollout, automated tests (800+), PostHog analytics, and Astro frontends for tenant dashboards.
- Results: Zero vulnerabilities in security audit, weekly deployments, multi-tenant RAG pipelines ready for production.
Ready to retrofit your own stack? Pair this guide with the AI platform development service for implementation support, or engage the AI security consulting offering to validate tenant isolation with structured security testing.
Read the full breakdown: Rails Platform Modernization Case Study
14. Conclusion & Next Steps
Multi-tenant SaaS architecture is a series of disciplined choices:
- RLS-first data modeling so the database enforces isolation.
- Strong authorization middleware so tenants can define roles safely.
- Thoughtful migrations so you don’t rewrite everything during hypergrowth.
- Performance planning so one noisy tenant doesn’t ruin everyone’s day.
- Testing + compliance automation so customer security reviews become routine, not panic moments.
Ready to implement multi-tenant architecture?
Option 1: Multi-Tenant Architecture Assessment
3-hour deep-dive reviewing your current schema, identifying isolation gaps, and providing a concrete migration roadmap.
What’s included:
- Current schema and isolation review
- RLS implementation strategy
- Performance and scaling recommendations
- Migration roadmap with timeline estimates
- Risk assessment for tenant data leakage
- Executive summary for leadership
Option 2: RLS Implementation Package
Hands-on implementation of row-level security for your existing platform.
What’s included:
- Schema design review and optimization
- RLS policy creation for all tenant tables
- Middleware and session management setup
- Connection pooling configuration
- Automated isolation testing suite
- Performance optimization and indexing
- Documentation and runbooks
Option 3: Full Multi-Tenant Platform Development
Build your multi-tenant SaaS platform from the ground up or modernize existing architecture.
What’s included:
- Everything in RLS Package, plus:
- Complete schema design and data modeling
- Authentication and authorization (Clerk, Auth0, custom)
- Tenant onboarding and provisioning workflows
- Admin portal and tenant management UI
- Billing integration (Stripe, usage-based pricing)
- Observability and tenant analytics
- Security testing and compliance prep
- 30-day post-launch support
View Platform Development Service →
Option 4: Multi-Tenant Security Audit
Validate your tenant isolation with comprehensive security testing.
What’s included:
- RLS policy review and testing
- Cross-tenant data leakage testing
- Authorization matrix testing
- Cache isolation validation
- Background job tenant context testing
- Compliance evidence preparation
- Detailed findings report with remediation guidance
Not sure which option fits?
Book a free 30-minute consultation to discuss your multi-tenant architecture challenges and recommended approach.
Free resources:
- Multi-Tenant SaaS Checklist - Complete multi-tenant architecture and RLS implementation guide
Related resources:
- AI Platform Security Guide - RLS patterns and tenant isolation
- Rails Modernization Strategy - Retrofitting multi-tenancy into legacy Rails
- RAG Architecture Guide - Multi-tenant RAG security
See Also
- AI Platform Security Guide - full system-wide architecture
- AI Agent Architecture - tool orchestration & guardrails
- LLM Security Guide - LLM-specific threat modeling
- Penetration Testing AI Platforms - how AI products are tested
- Multi-Tenant SaaS Architecture - tenant isolation & RLS
- RAG Architecture Guide - retrieval and semantic search
We’ve delivered this playbook repeatedly-from Rails platforms to Next.js/Astro frontends with PostHog analytics. If you’re staring at a tangle of tenant-specific schemas or prepping for your first enterprise deal, let’s talk.
About the Author
Matt Owens is a principal engineer with 15 years shipping production systems and 4 years at Tesla. He leads CodeWheel, delivering multi-tenant SaaS platforms with RLS-first security, Astro frontends, and PostHog instrumentation. Connect on LinkedIn or learn more about Matt and CodeWheel.





