Security Testing - AI Platforms - Vulnerability Assessments
Penetration testing that mirrors how AI platforms actually break
Run by an independent architect who blends OWASP reviews with AI-specific attack chains
Security testing that targets the way AI platforms actually fail. With 15 years shipping production systems and fixing security issues for high-growth engineering teams, every penetration test blends OWASP methodology, application-layer testing, and AI-specific attack chains so you leave with a remediation plan that matches your stack, plus the PDF report stakeholders expect.
Exploit payloads and jailbreak corpora stay private for safety reasons. You get the findings, evidence, and fixes-without publishing the exploit kit.
That means web apps, APIs, cloud infrastructure, and network security reviews alongside prompt injection, RAG leakage, and agent abuse scenarios. No agency markup. Direct access to the person doing the work. Need broader AI Security Consulting or dedicated Prompt Injection Defense ? Those plug into this same playbook.
Looking for AI Security Consulting or Prompt Injection Testing instead? CodeWheel covers those too.
Honest stats
15 Years
Production engineering (Tesla & startups)
Independent Architect
No handoffs or account managers
Security Built In
Testing integrated with development
Pricing scoped after reviewing your stack and attack surface.
Anonymized examples
What recent tests uncovered
Multi-tenant RAG
Caught cross-tenant retrieval via weak metadata filters; patched query scopes and replayed hostile corpora before audit.
Agent tool abuse
Found agent-triggered billing mutation without confirmation; added RBAC + confirmation workflow and rollback path.
Prompt injection
Detected jailbreak chain that bypassed content policy; added guardrails and regressions before GA.
Testing methodology
How CodeWheel tests: tools, techniques & process
Automation provides coverage, but impact comes from the humans behind it. The stack stays lean on purpose-Kali Linux recon utilities, OWASP ZAP, and nuclei templates guided by OWASP checklists-then manual exploitation stitches the AI attack chains together.
Scope & Goals
Walk the product, align on timelines, and decide how aggressive testing should be so we can focus on the riskiest flows first.
Recon & Instrumentation
Kali Linux recon tooling (ffuf, dirsearch, dnsenum) plus nuclei sweeps highlight exposed assets while staging mirrors production.
Application & API Testing
OWASP ZAP with custom wordlists plus nuclei templates runs through OWASP-style checklists even before we purchase dedicated tooling.
AI & Prompt Injection Playbooks
Custom adversarial prompt libraries, RAG replay harnesses, and jailbreak scripts pressure-test LLM tooling and agent workflows.
Manual Exploitation & Pairing
Hands-on testing blends OWASP techniques with AI-specific attack chains. Findings land live in Slack/Email so fixes start immediately.
Report & Retest
Receive prioritized findings with mitigations. We retest within 30 days and document closure for investors, auditors, or customers.
Deliverables
What you get
Every engagement includes a report with executive summary, technical details, reproduction steps, and remediation guidance. Screenshots, API payloads, and infrastructure findings are ready to share with customers or investors.
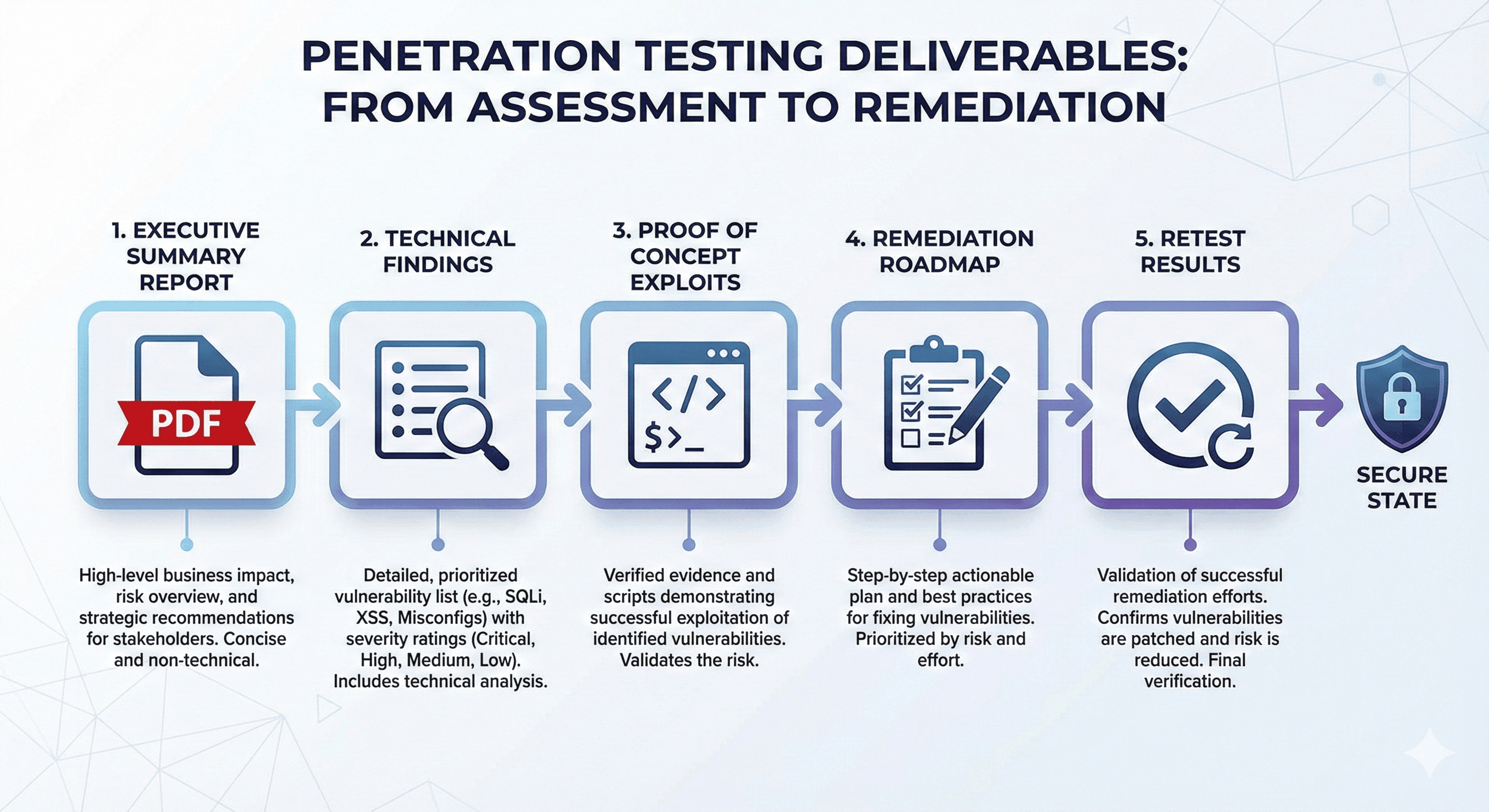
- Executive summary explaining impact in plain language.
- Detailed technical report covering OWASP results and AI-specific attacks.
- CSV/Markdown issue tracker with severity, reproduction steps, and fix recommendations.
- 30-day retest window to confirm remediation plus Slack/Email updates.
- Optional pairing sessions to implement fixes faster.
Testing scope
What CodeWheel tests
Coverage spans web apps, APIs, cloud infrastructure, and AI-specific surfaces. Each engagement is scoped to your stack.
Web applications
OWASP Top 10, business logic abuse, authentication flaws, and front-end/back-end misconfigurations.
Includes SPAs, multi-tenant dashboards, and Next.js/Supabase stacks.
APIs & microservices
REST/gRPC/GraphQL testing for authorization bypass, mass assignment, injection, rate limiting, and agent tool misuse.
Covers internal/external APIs plus partner integrations.
Cloud & infrastructure
AWS, Vercel, and Cloudflare config reviews, CI/CD pipeline testing, container scanning, and network segmentation.
Identifies privilege escalation paths, leaked credentials, and insecure defaults.
AI & prompt injection
Prompt injection attacks, RAG leakage, agent misuse, and LLM jailbreak simulations with automated replay harnesses.
See the dedicated prompt injection service .
Automation suite
API testing that runs in your CI/CD
Not a generic scanner. OWASP ZAP tuned for REST APIs, MCP agent routes, and CI/CD pipelines so the payloads keep running after the engagement.
API-first design
OWASP ZAP tuned for REST, GraphQL, and MCP routes-payloads match how your services actually behave.
- JSON payload manipulation
- API key authentication coverage
- Multi-tenant testing scenarios
- Business logic validation
Custom attack scripts
Hunts for auth bypass, mass assignment, IDOR, input validation gaps, and rate limiting issues.
- Code analysis before scripting payloads
- Auth logic review
- Input validation analysis
- Rate limit effectiveness checks
CI/CD native
Ship the suite with your pipelines so every PR gets the same scrutiny.
- Docker-based runners
- Machine-readable output (JSON, SARIF)
- GitHub Actions integration
- Automatic PR commenting
Low false positives
Custom scripts hit production-grade attack paths, not theoretical ones.
- Real endpoints and environments
- Actual authentication patterns
- Concrete authorization logic
- Specific input validation permutations
Want to see it?
30-minute walkthrough tailored to your stack
I'll show you the OWASP ZAP automation, replay harnesses, and CI/CD wiring.
Why CodeWheel
Builder who breaks things
CodeWheel builds production systems and then tests them. That means full-stack context, AI attack chains included, and reports written for founders, engineers, and auditors.
Full-stack background
15 years shipping production systems (Tesla, SaaS, agencies). Findings come with fixes, not just reports.
AI-specific expertise
Prompt injection, RAG leakage, agent abuse, LLM jailbreaks-custom playbooks, not generic scanners.
Direct access
No account managers. I scope, run, and deliver every engagement myself with live Slack updates.
Results in production
What shipping with security actually looked like
A few anonymized wins pulled from recent engagements. These are the checkpoints I report on-not just the tools used.
Custom agent + RAG launch
6 critical vulns patched pre-audit
- Multi-tenant RAG workflow leaking prompts + cross-tenant data
- Missing rate limits/API throttles on critical inference endpoints
- Metadata filters + hostile corpus replays in staging before go-live
- Cleared enterprise security review on first submission
SaaS modernization
Zero findings on external pen test
- Rails + Supabase stack upgrade with rebuilt auth/session handling
- 800+ automated tests covering APIs, jobs, and tenant workflows
- External pen-test closed with zero findings, procurement reactivated
- Support backlog dropped once AI summaries + regression tests landed
Agent operations platform
25 workflows live, 0 security regressions
- MCP agents for finance/support with tool allowlists + rate limits
- Sandboxed exec + centralized logging before each pilot stage
- Pen testing + retests baked into every rollout checkpoint
- 25 automated workflows live with zero prompt/ops regressions
Engagement models
How we can work together
Scoped to your stage. Every engagement includes detailed reports, remediation guidance, and retesting within 30 days.
Quick Assessment
Fast vulnerability review
- 60-minute session
- Architecture review
- Top 5 risks + next steps
- Great before fundraising or launch
Full Security Test
Comprehensive engagement
- 2-3 week engagement
- OWASP + AI-specific testing
- Detailed reports + retest validation
- Best for pre-launch
Platform Build + Security
Next.js AI platform with security built in
- RAG or AI platform build
- Auth, billing, and observability
- Security testing and hardening included
Ongoing Partnership
Continuous testing
- Monthly or quarterly cadence
- New feature testing before launch
- On-call support
- Flexible 3-month minimum
FAQ
Common questions
Do you work independently?
Yes. You work directly with me. If a project needs specialized tooling or extra coverage, I bring in trusted partners with full transparency.
Do you help fix the issues you find?
Absolutely. Every report includes remediation guidance. I pair with your team to implement fixes and validate through retesting. If you want me to handle fixes directly, we can scope that separately.
Does this satisfy compliance requirements?
I bridge the gap between engineering and audit. I provide the technical evidence (test reports, architecture diagrams) your auditor needs for security readiness, but I do not issue formal compliance certificates. For third-party attestations, I can refer you to specialists.
What access do you need to start?
Role-based accounts (admin + standard user), API docs, staging environment if possible, and a list of out-of-bounds areas. All engagements are covered by NDA.
What happens if you find a critical issue?
You hear about it immediately-even if it's 3 AM Pacific. I provide reproduction steps, immediate mitigations, and help with communication plans. Critical findings don't wait for the final report.
Related services
Need the broader security + platform stack too?
Penetration testing is one slice of the CodeWheel studio. Plug into the rest when you're ready.
AI Security Consulting
Ongoing threat modeling, security architecture, and incident rehearsal so you're ready for audits and enterprise deals.
Explore AI security consultingPrompt Injection Testing
Focused adversarial suites for RAG/chat/agent surfaces. Hardens guardrails and logging before anyone sees production prompts.
View prompt injection servicesNext.js AI Platform Development
End-to-end RAG/Next.js builds with security + observability baked in so pen testing becomes an ongoing practice, not a fire drill.
See the build processReady to get started?
Share your architecture, security requirements, and timeline. We'll outline scope, approach, and fixed pricing. If we're not the right fit, we'll tell you.
CodeWheel doesn't just identify risks—we help fix them through architecture reviews, remediation pairing, and secure platform builds.
For methodology details, read our complete penetration testing guide.
Serving companies across the San Francisco Bay Area, Silicon Valley, and remote teams worldwide.
